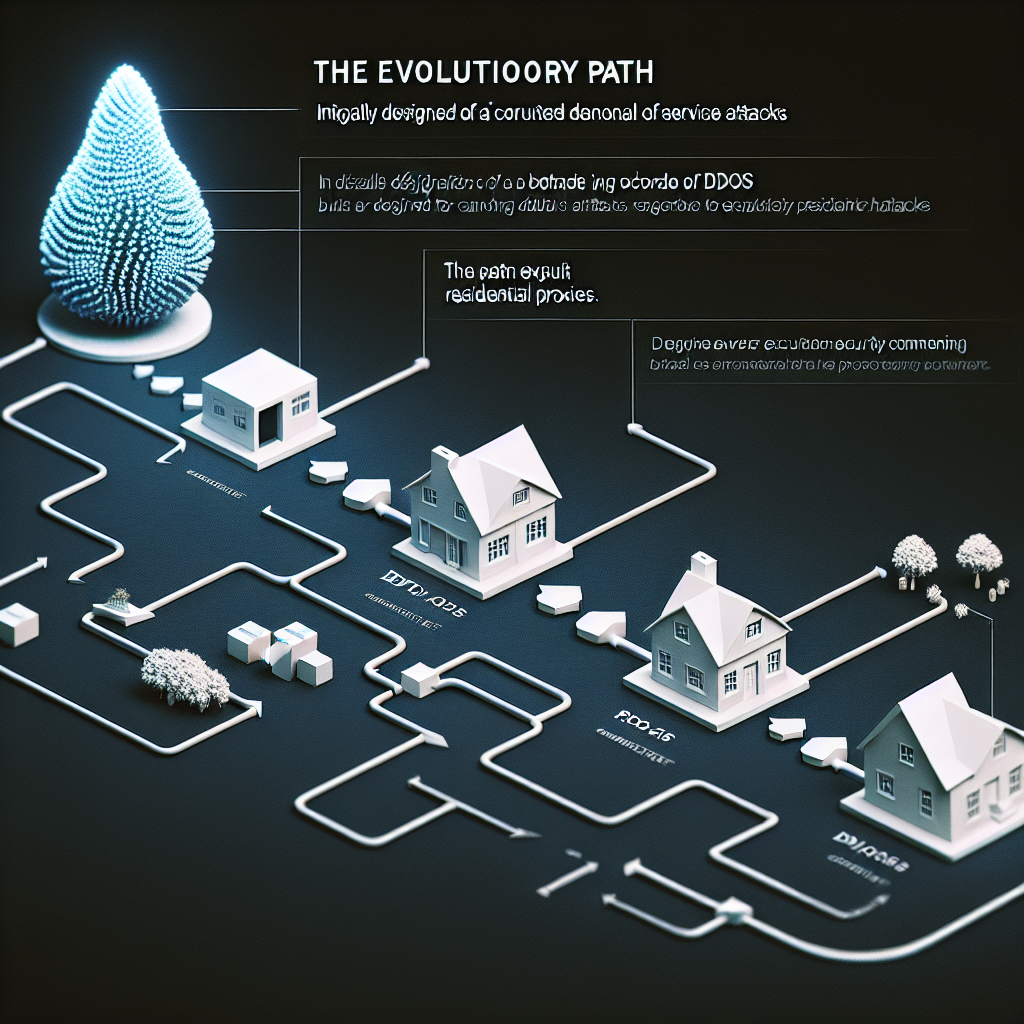
The Aisuru botnet, initially notorious for executing record-breaking distributed denial-of-service (DDoS) attacks, has transitioned towards a more covert yet lucrative operation model by utilizing infected Internet of Things (IoT) devices to power residential proxy services. This evolution underscores a significant trend within the cybersecurity landscape, wherein cybercriminals leverage compromised devices to anonymize their internet traffic, thereby facilitating large-scale data harvesting initiatives. Such activities have become increasingly intertwined with the artificial intelligence (AI) sector, as data scraping efforts utilize these residential proxies to evade detection, presenting new challenges for cybersecurity experts.
The primary goal of the Aisuru botnet’s transition from DDoS attacks to residential proxy services is to create a sustainable revenue stream while minimizing the risks associated with high-profile attacks. This shift can be achieved through the rental of compromised devices to proxy services, allowing cybercriminals to operate with relative anonymity. By obscuring the origin of their internet traffic, these actors can conduct malicious activities—including data scraping for AI projects—without the immediate threat of detection or mitigation by cybersecurity measures.
However, it is important to note that this model is not without its limitations. The reliance on compromised devices raises ethical concerns and could provoke regulatory scrutiny as authorities intensify their efforts to combat cybercrime.
The intersection of AI and cybersecurity is poised for significant evolution as advancements in AI technologies continue to shape the tactics employed by cybercriminals. The ongoing proliferation of data scraping activities, particularly those that support AI training datasets, will likely result in increased competition for resources among malicious actors. Moreover, as AI systems become more sophisticated, they may enable more advanced techniques for evading detection, necessitating rapid adaptation by cybersecurity experts.
In the future, we may also see a rise in legislative measures aimed at curbing the use of residential proxies for malicious purposes, alongside the development of more robust detection mechanisms for identifying and mitigating threats posed by botnets like Aisuru. Cybersecurity professionals will need to remain vigilant and proactive in their strategies, leveraging emerging technologies and methodologies to counteract the evolving landscape of cyber threats.
Disclaimer
The content on this site is generated using AI technology that analyzes publicly available blog posts to extract and present key takeaways. We do not own, endorse, or claim intellectual property rights to the original blog content. Full credit is given to original authors and sources where applicable. Our summaries are intended solely for informational and educational purposes, offering AI-generated insights in a condensed format. They are not meant to substitute or replicate the full context of the original material. If you are a content owner and wish to request changes or removal, please contact us directly.
Source link :